Students’ vulnerability to cybercrime: implications for cybersecurity in the global south
DOI:
https://doi.org/10.33830/ijdmde.v2i2.11869Keywords:
Cybercrime, Cybercrime Vulnerability, Global South, Higher Education, Protection Motivation TheoryAbstract
This conceptual study examines key issues around students’ vulnerability to cybercrimes in the Global South. The increasing digitalization of education has exposed students in the Global South to heightened risks of cybercrime. Limited cybersecurity awareness, inadequate digital infrastructure, and socio-economic vulnerabilities make students particularly susceptible to cyber threats such as phishing, identity theft, and online fraud. This article examines the key factors contributing to students’ exposure to cybercrime, including gaps in digital literacy, institutional cybersecurity policies, and the role of social and economic disparities. It also explores the broader implications for cybersecurity frameworks in the Global South, emphasizing the need for enhanced policy interventions, education reforms, and multi-stakeholder collaborations. By addressing these challenges, governments, educational institutions, and technology providers can foster a safer digital environment for students, ultimately strengthening overall cybersecurity resilience in the region. The study underscores the need for targeted cybersecurity awareness programmers and institutional policies to enhance students’ online safety.
References
Abah, J. A. (2019). Theoretical and conceptual framework for digital inclusion among mathematics education students in Nigeria. Global perspectives on educational issues, 1(1), 79-111.
Abdulla, R. M., Faraj, H. A., Abdullah, C. O., Amin, A. H., & Rashid, T. A. (2023). Analysis of social engineering awareness among students and lecturers. IEEE Access, 11, 101098-101111. https://doi.org/10.1109/ACCESS.2023.3311708
Abraham, S., & Chengalur-Smith, I. (2010). An overview of social engineering malware: Trends, tactics, and implications. Technology in Society, 32(3), 183-196. https://doi.org/10.1016/j.techsoc.2010.07.001
Adeniran, A. A., Adeniran, A. O., Familusi, O. B., & Adedayo, O. (2024). The Outlook of Cyber Security in African Businesses: Issues and Way-Out. Management analytics and social insights, 1(2), 260-271. https://doi.org/10.22105/masi.v1i2.54
African Union. (2020). African Union Convention on Cyber Security and Personal Data Protection. Retrieved April 1, 2025, from https://au.int/en/treaties/african-union-convention-cyber-security-and-personal-data-protection
African Union. (2020). Cybersecurity in Africa: A report on the state of cybercrime. African Union.
Agnew, R. (1992). Foundation for a General Strain Theory of Crime and Delinquency, Criminology, 30, 47-87.
Akinwotu, E. (2024). FBI director urges Nigeria to do more to combat the rise of sextortion. https://www.npr.org/2024/06/14/nx-s1-5006112/the-issue-of-sextortion-was-high-on-the-agenda-when-the-fbi-director-traveled-to-nigeria
Akinyetun, T. S. (2021). Poverty, cybercrime and national security in Nigeria. Journal of Contemporary Sociological Issues, 1(2), 86-109. https://doi.org/10.19184/csi.v1i2.24188
Alam, S. S., Ahsan, N., Kokash, H. A., Alam, S., & Ahmed, S. (2024). A students’ behaviors in information security: Extension of Protection Motivation Theory (PMT). Information Security Journal: A Global Perspective, 1-23. https://doi.org/10.1080/19393555.2024.2408264
Anazodo, R. O. (2025). Cyber security administration in developing countries: a Nigerian perspective. International Journal of Finance, Accounting and Management Studies, 1(4), 122-139. http://www.ijfams.com/index.php/ijfams/article/download/55/55
Anyanwu, U. S. (2024). Youth’s Unemployment and Cybercrime in Nigeria. Canadian Social Science, 20(5), 69-78. https://dx.doi.org/10.3968/13574
Aphane, M. P., & Mofokeng, J. T. (2020). Critical Analysis of Strategies Towards Creating an Adequate Level of Awareness on Cybercrime among the Youth in Gauteng Province. International Journal of Criminology & Sociology, 9, 1385-1396.
Ayandele, O., & Popoola, O. (2022). Yahoo Yahoo: Cyber-enabled crime and criminality in Nigeria. SSRN. https://doi.org/10.2139/ssrn.4123456
Bada, M., & Nurse, J. R. (2019). Developing cybersecurity education and awareness programmes for small-and medium-sized enterprises (SMEs). Information & Computer Security, 27(3), 393-410. https://doi.org/10.6000/1929-4409.2020.09.159
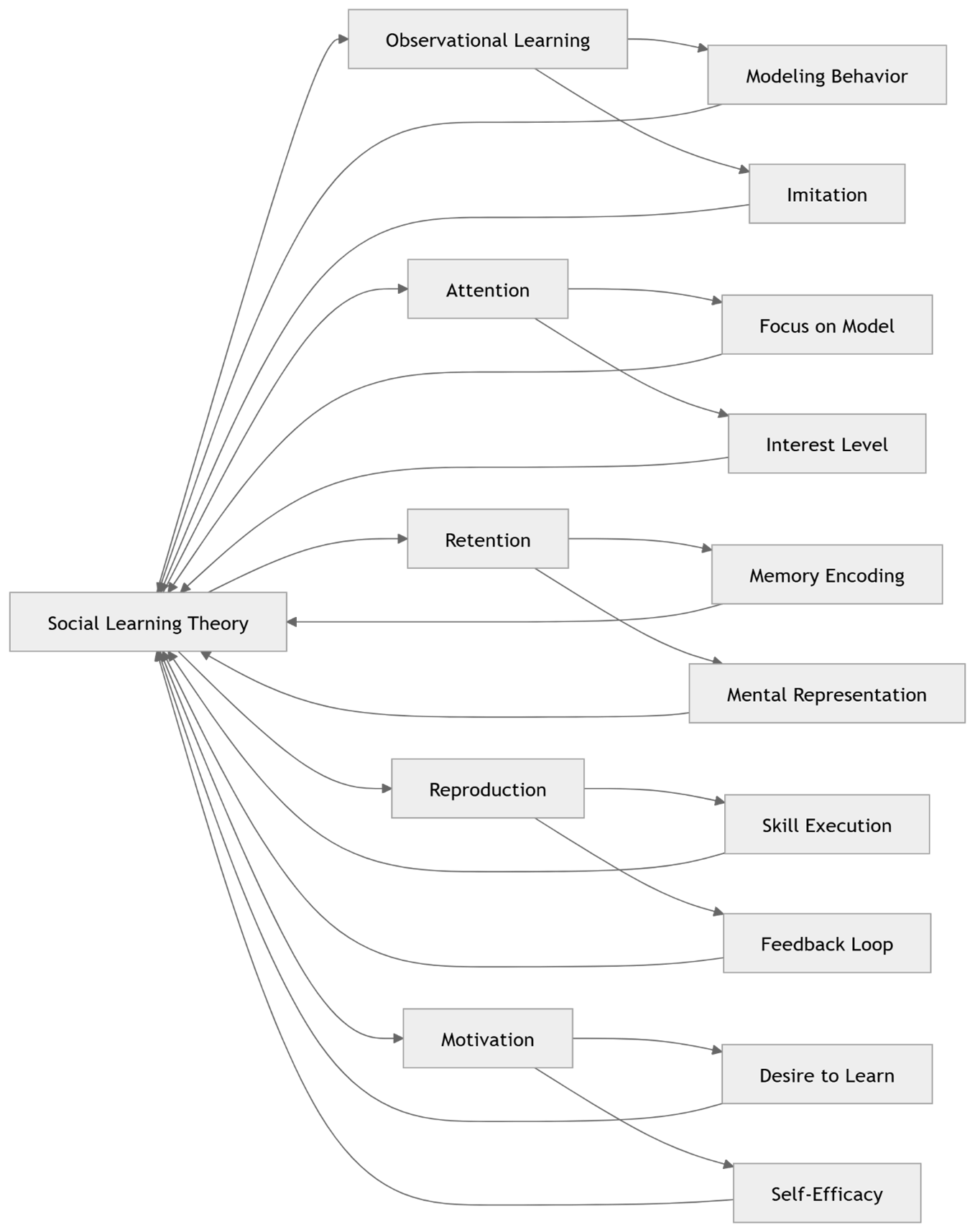
Bandura, A. (1977). Social learning theory. Englewood Cliffs, NJ: Prentice-Hall.
Bello, M., & Griffiths, M. (2021). Routine activity theory and cybercrime investigation in Nigeria: how capable are law enforcement agencies? Rethinking Cybercrime: Critical Debates, 213-235.
Boateng, R., Olumide, L., Isabalija, R. S., & Budu, J. (2011). Sakawa-cybercrime and criminality in Ghana. Journal of Information Technology Impact, 11(2), 85-100.
Bottyán, L. (2023). Cybersecurity awareness among university students. Journal of Applied Technical and Educational Sciences, 13(3), 363-363. https://doi.org/10.24368/jates363
Bougaardt, G., & Kyobe, M. (2011). Investigating the factors inhibiting SMEs from recognizing and measuring losses from cybercrime in South Africa. In ICIME 2011-Proceedings of the 2nd International Conference on Information Management and Evaluation: ICIME 2011 Ryerson University (p. 62).
Bradshaw, S., & Howard, P. N. (2019). The global disinformation order: 2019 global inventory of organised social media manipulation. (Working Paper 2019.2). https://digitalcommons.unl.edu/scholcom/207/
Broadhurst, R. (2006). Developments in the global law enforcement of cyber‐crime. Policing: An International Journal of Police Strategies & Management, 29(3), 408-433. https://doi.org/10.1108/13639510610684674
Broadhurst, R., Grabosky, P., Alazab, M., & Bouhours, B. (2013). Organizations and cybercrime. Available at SSRN 2345525.
Button, M., Johnston, L., & Frimpong, K. (2008). The fraud review and the policing of fraud: laying the foundations for a centralized fraud police or counter fraud executive?.Policing: A Journal of Policy and Practice, 2(2), 241-250.
Calderaro, A., & Craig, A. J. (2020). Transnational governance of cybersecurity: policy challenges and global inequalities in cyber capacity building. Third world quarterly, 41(6), 917-938. https://cybilportal.org/wp-content/uploads/2020/10/CalderaroCraigTWQ_Transnational-governance-of-cybersecurity-policy-challenges-and-global-inequalities-in-cyber-capacity-building.pdf
Campbell, Q., & Kennedy, D. M. (2012). The psychology of computer criminals. Computer security handbook, 12-1.
Cheng, E. C., & Wang, T. (2022). Institutional strategies for cybersecurity in higher education institutions. Information, 13(4), 192. https://doi.org/10.3390/info13040192
Chukwuma, E., & Olaniyi, O. (2022). Social media usage and cyber vulnerabilities among undergraduates in Nigeria. African Journal of Information Systems, 14(3), 220-234.
CISA. (2025). Cybersecurity Best Practices. Cybersecurity and Infrastructure Security Agency. Retrieved March 26, 2025, from https://www.cisa.gov/topics/cybersecurity-best-practices
Cojocariu, A. C., Verzea, I., & Chaib, R. (2020). Aspects of cyber-security in higher education institutions. In Innovation in Sustainable Management and Entrepreneurship: 2019 International Symposium in Management (SIM2019) (pp. 3-11). Springer International Publishing.
Dennis, M. A. (2025). Cybercrime: Definition, Statistics, & Examples. Britannica. Retrieved March 26, 2025, from https://www.britannica.com/topic/cybercrime
DiPLO. (2021). ECOWAS Regional Cybersecurity and Cybercrime Strategy. Retrieved April 1, 2025, from https://www.diplomacy.edu/resource/report-stronger-digital-voices-from-africa/cybersecurity-cybercrime-africa-continental-regional-policies/
Donalds, C., Barclay, C., & Osei-Bryson, K. M. (2022). Cybercrime and Cybersecurity in the Global South: Concepts, Strategies and Frameworks for Greater Resilience. Routledge.
Donovan, K. P., Frowd, P. M., & Martin, A. K. (2016). ASR Forum on surveillance in Africa: Politics, histories, techniques. African Studies Review, 31-37.
Egete, D. O., Ele, B. I., & Eko, M. C. E. (2023). Synopsis of Cybersecurity and Risks Associated with Cybercrime to Susceptible and Blameless Global Citizenries. Applied Sciences, 1(5), 475-487. https://doi.org/10.59324/ejtas.2023.1(5).37
Ehimen, O. R., & Bola, A. (2010). Cybercrime in Nigeria. Business Intelligence Journal, 3(1), 93-98.
Ere-Mendie, A. J. (2023). Nigerian Data Policies. The Mediation of Sustainability: Development Goals, Social Movements, and Public Dissent, 161.
European Union Cyber Diplomacy Initiative. (2025). A safer digital Ghana. EU Cyber Direct. Retrieved April 1, 2025, from https://eucyberdirect.eu/good-cyber-story/a-safer-digital-ghana
Europol. (2024). Internet Organised Crime Threat Assessment (IOCTA): Strategic, policy and tactical updates on the fight against cybercrime. https://www.europol.europa.eu/publications-events/main-reports/iocta-report
Federal Republic of Nigeria, (2021). National cybersecurity policy and strategy. https://cert.gov.ng/ngcert/resources/NATIONAL_CYBERSECURITY_POLICY_AND_STRATEGY_2021.pdf
Floyd, D. L., Prentice‐Dunn, S., & Rogers, R. W. (2000). A meta‐analysis of research on protection motivation theory. Journal of applied social psychology, 30(2), 407-429.
Fox, J. (2024). Top Cybersecurity Statistics for 2024. Cobalt. Retrieved March 26, 2025, from https://www.cobalt.io/blog/cybersecurity-statistics-2024
Freedom House. (2022). Freedom on the net 2022: https://freedomhouse.org/sites/default/files/2022-10/FOTN2022Digital.pdf
Henry, N., & Umbach, R. (2024). Sextortion: Prevalence and correlates in 10 countries. Computers in Human Behavior, 158, 108298. https://doi.org/10.1016/j.chb.2024.108298
Holt, T., & Bossler, A. (2015). Cybercrime in progress: Theory and prevention of technology-enabled offenses. Routledge.
Ibrahim, A. (2016). Cybercrime (Prohibition, Prevention Etc) Act, 2015: Issues and Challenges in Nigeria. In Draft Paper Presented at the 49th Annual Nigerian Law Teachers’ Conference at Nasarawa State University, Keffi on behalf of Usman Danfodio University Sokoto, 22nd-27th May (pp. 15-16).
Ibrahim, Y. A., Ishaya, A. O., Yusuf, M., Nancy, I., Bijik, H. A., & Aiyedogbon, S. F. (2024). Cybersecurity and cybercrimes in Nigeria: An overview of challenges and prospects. In 2024 International Conference on Science, Engineering and Business for Driving Sustainable Development Goals (SEB4SDG) (pp. 1-7). IEEE.
Idowu, O. A., & Madaki, M. (2021). Cybercrimes and challenges of cyber-security in Nigeria. International Journal of Sociology and Development, 3(1), 45-67.
Igba, I. D., Igba, E. C., Nwambam, A. S., Nnamani, S. C., Egbe, E. U., & Ogodo, J. V. (2018). Cybercrime among university undergraduates: Implications on their academic achievement. International Journal of Applied Engineering Research, 13(2), 1144-1154. https://www.ripublication.com/ijaer18/ijaerv13n2_43.pdf
Iji, C. O., & Abah, J. A. (2019). Internet skills as a measure of digital inclusion among mathematics education students: Implications for sustainable human capital development in Nigeria. International Journal of Education and Knowledge Management (IJEKM), 2(1), 1-16.
Interpol. (2024). Inside INTERPOL’s probe into cyber-enabled human trafficking. https://www.interpol.int/en/News-and-Events/News/2024/Inside-INTERPOL-s-probe-into-cyber-enabled-human-trafficking
Interpol. (2021). INTERPOL launches initiative to fight cybercrime in Africa. Retrieved April 1, 2025, from https://www.interpol.int/en/News-and-Events/News/2021/INTERPOL-launches-initiative-to-fight-cybercrime-in-Africa
Kaspersky. (2025). What is cybercrime? How to protect yourself. Kaspersky. Retrieved March 26, 2025, from https://www.kaspersky.com/resource-center/threats/what-is-cybercrime
Kayomb, M. J. (2024). Phishing attack awareness amongst users at a university of technology in the Western Cape (Doctoral dissertation, Cape Peninsula University of Technology).
Khan, N. F., Ikram, N., & Saleem, S. (2023). Effects of socioeconomic and digital inequalities on cybersecurity in a developing country. Security Journal, 1, 1-31. https://doi.org/10.1057/s41284-023-00375-4
Kidd, C (2025). Vulnerabilities, Threats & Risk Explained. Retrieved April 1, 2025, from https://www.splunk.com/en_us/blog/learn/vulnerability-vs-threat-vs-risk.html
Kshetri, N. (2016). Cybercrime and Cybersecurity in India: Causes, Consequences and Implications for the Future. Crime, Law and Social Change, 66(3), 313–338. https://libres.uncg.edu/ir/uncg/f/N_Kshetri_Cybercrime_2016.pdf
Kshetri, N. (2019) Cybercrime and Cybersecurity in Africa. Journal of Global Information Technology Management, 22(2), 77-81. https://doi.org/10.1080/1097198X.2019.1603527
Kumah, P. K., Asiedu, H. B., Obeng, C., & Senior, F. A. O. (2024). Poverty as a catalyst for cybercrime: evidence from Agona Swedru, Ghana. E-Journal of Humanities, Arts and Social Sciences, 5(14), 2582-2596. https://doi.org/10.38159/ehass.202451410
Kundi, G. M., Nawaz, A., & Akhtar, R. (2014). Digital revolution, cyber-crimes and cyber legislation: A challenge to governments in developing countries. Journal of Information Engineering and Applications, 4(4), 61-71. https://core.ac.uk/download/pdf/234677092.pdf
Levi, M., Doig, A., Gundur, R., Wall, D., & Williams, M. (2017). Cyberfraud and the implications for effective risk-based responses: themes from UK research. Crime, Law and Social Change, 67, 77-96. https://doi.org/10.1007/s10611-016-9648-0
Lusthaus, J. (2024). Reconsidering crime and technology: what is this thing we call cybercrime? Annual Review of Law and Social Science, 20(1), 369-385. https://doi.org/10.1146/annurev-lawsocsci-041822-044042
Meso, P., Ding, Y., & Xu, S. (2013). Applying protection motivation theory to information security training for college students. Journal of Information Privacy and Security, 9(1), 47-67. https://doi.org/10.1080/15536548.2013.10845672
Morland, S. (2024). Latin America and Caribbean launch regional alliance against organized crime. Retrieved April 1, 2025, from https://www.reuters.com/world/americas/latin-america-caribbean-launch-regional-alliance-against-organized-crime-2024-12-12/
Mphatheni, M. R., & Maluleke, W. (2022). Cybersecurity as a response to combating cybercrime: Demystifying the prevailing threats and offering recommendations to the African regions. International journal of research in business and social science, 11(4), 384-396. https://doi.org/10.20525/ijrbs.v11i4.1714
Munoriyarwa, A., & Mare, A. (2023). Digital Surveillance in Southern Africa. Springer International Publishing AG.
Muraina, I. O., Agoi, M. A., Adedokun, A. A., & Oyeniran, B. A. (2022). Social engineering pressures in Nigeria institutions: Why students are the main targets? Al-hikmah Journal of Education, 9(2), 313-325.
Mwangi, T., Asava, T., & Akerele, I. (2022). Cybersecurity threats in africa. In The Palgrave handbook of sustainable peace and security in Africa (pp. 159-180). Cham: Springer International Publishing.
NetMission.Asia. (2024). Cybersecurity challenges in South Asia: India’s largest data breaches and cyberattack on Pakistan’s National Institutional Facilitation Technologies (NIFT). Retrieved April 1, 2025, from https://netmission.asia/2024/04/08/netmission-case-study-series-2024-cybersecurity-challenges-in-south-asia-indias-largest-data-breaches-and-cyberattack-on-pakistans-national-institutional-facilitation-technologie
Nzeakor, O. F., Nwokeoma, B. N., Hassan, I., Ajah, B. O., & Okpa, J. T. (2022). Emerging trends in cybercrime awareness in Nigeria. International Journal of Cybersecurity Intelligence & Cybercrime, 5(3), 41-67.
Oduro-Frimpong, J. (2014). Sakawa rituals and cyberfraud in Ghanaian popular video movies. African Studies Review, 57(2), 131-147. https://doi.org/10.1017/asr.2014.51
OECD. (2024). New perspectives on measuring cybersecurity. https://one.oecd.org/document/DSTI/CDEP/MADE(2023)14/FINAL/en/pdf
Ogunleye, Y. O., Ojedokun, U. A., & Aderinto, A. A. (2019). Pathways and Motivations for Cyber Fraud Involvement among Female Undergraduates of Selected Universities in South-West Nigeria. International Journal of Cyber Criminology, 13(2), 309-325. https://doi.org/10.5281/zenodo.3702333
Ogunyemi, A. A. (2024). Cyber Risks and the Nigerian Business Sector: A Critical Analysis of the Emerging Cyber Insurance Market in Nigeria. ACU Journal of Social Sciences, 3(1), 1-21. https://ajss.acu.edu.ng/index.php/ajss/article/download/145/87
Ojedokun, U. A., & Eraye, M. C. (2012). Socioeconomic lifestyles of the yahoo-boys: A study of perceptions of university students in Nigeria. International Journal of Cyber Criminology, 6(2), 1001. https://www.cybercrimejournal.com/pdf/Ojedokun&Eraye2012julyijcc.pdf
Ojugo, A. A., & Eboka, A. O. (2021). Empirical evidence of socially-engineered attack menace among undergraduate smartphone users in selected Universities in Nigeria. International Journal, 10(3), 34-54. https://doi.org/10.11591/ijeecs.v28.i3.pp1756-1765
Okeke, N., & Onyekachukwu, I. O. (2024). Cybercrime and digital fraud among university students in Lagos, Nigeria: Socio-Economic Drivers and Prevention Approaches. Journal of Research in Social Science and Humanities, 3(9), 13-21. https://doi.org/10.56397/jrssh.2024.09.02
Olayemi, O. J. (2014). A socio-technological analysis of cybercrime and cyber security in Nigeria. International Journal of Sociology and Anthropology, 6(3), 116. https://academicjournals.org/article/article1392996162_Olayemi.pdf
Olomu, S. (2023, November, 23). Nigeria tightens laws to tackle yearly cyber-crime losses of $500m. iTWeb Africa. https://itweb.africa/content/mYZRXM9gxVNvOgA8
Onuora, A. C., Uche, D. C., Ogbunude, F. O., & Uwazuruike, F. O. (2017). The challenges of cybercrime in Nigeria: an overview. AIPFU Journal of School of Sciences, 1(2), 6-11.
Onyema, E. M., Edeh, C. D., Gregory, U. S., Edmond, V. U., Charles, A. C., & Richard-Nnabu, N. E. (2021). Cybersecurity awareness among undergraduate students in Enugu Nigeria. International Journal of Information Security, Privacy and Digital Forensics, 5(1), 34-42.
Osho, O., & Onoja, A. D. (2015). National cyber security policy and strategy of Nigeria: a qualitative analysis. International Journal of Cyber Criminology, 9(1), 120-143. https://doi.org/10.5281/zenodo.22390
Otozi, U. J., Ephraim, B., Yinka, A. I., & Hyginus, M. C. (2024). Cybercrime and its negative effects in developing countries. Journal of Mobile Computing and Application, 11(4), 10-16. https://doi.org/10.9790/0050-11041016
Parrish, A., Impagliazzo, J., Raj, R. K., Santos, H., Asghar, M. R., Jøsang, A., ... & Stavrou, E. (2018). Global perspectives on cybersecurity education for 2030: a case for a meta-discipline. In Proceedings companion of the 23rd annual ACM conference on innovation and technology in computer science education (pp. 36-54).
Pieterse, H. (2021). The cyber threat landscape in South Africa: A 10-year review. The African Journal of Information and Communication, 28, 1-21. https://doi.org/10.23962/10539/32213
Pryimenko, L. (2024). 12 Cybersecurity Best Practices & Measures to Prevent Cyber Attacks. Syteca. Retrieved March 26, 2025, from https://www.syteca.com/en/blog/best-cyber-security-practices
Rogers, R. W. (1975). A protection motivation theory of fear appeals and attitude change1. The journal of psychology, 91(1), 93-114. https://doi.org/10.1080/00223980.1975.9915803
Rufai, A., Modi, S., & Wadata, B. (2021). A survey of cyber-security practices in Nigeria. International Research Journal of Advanced Engineering and Science, 222-226. http://irjaes.com/wp-content/uploads/2020/10/IRJAES-V5N3P350Y20.pdf
Srivastava, A. K., Singh, A. V., & Som, S. (2024). Critical Analysis of Cybersecurity Awareness Programs in School Education. Library of Progress-Library Science, Information Technology & Computer, 44(3), 18282-182303. https://doi.org/10.48165/bapas.2024.44.2.
Świątkowska, J. (2020). Tackling cybercrime to unleash developing countries’ digital potential. Pathways for Prosperity Commission Background Paper Series, 33, 2020-01. https://pathwayscommission.bsg.ox.ac.uk/sites/default/files/2020-01/tackling_cybercrime_to_unleash_developing_countries_digital_potential.pdf
Tade, O., & Aliyu, I. (2011). Social organization of Internet fraud among university undergraduates in Nigeria. International Journal of Cyber Criminology, 5(2), 860-875. https://www.cybercrimejournal.com/pdf/tadealiyui2011julyijcc.pdf
Tambo, E., & Adama, K. (2017). Promoting cybersecurity awareness and resilience approaches, capabilities and actions plans against cybercrimes and frauds in Africa. International Journal of Cyber-Security and Digital Forensics, 6(3), 126-138. https://doi.org/10.17781/P002278
Tzani, C., Ioannou, M., Fletcher, R., & Williams, T. J. V. (2024). Psychological factors leading to sextortion: The role of personality, emotional factors and sexual needs in victimisation. Computers in Human Behavior, 159, 108323. https://doi.org/10.1016/j.chb.2024.108323
Uchendu, B., Nurse, J. R., Bada, M., & Furnell, S. (2021). Developing a cyber security culture: Current practices and future needs. Computers & Security, 109, 102387. https://doi.org/10.1016/j.cose.2021.102387
Wall, D. S. (2024). Cybercrime: The transformation of crime in the information age. John Wiley & Sons.
World Bank. (2025). Enhancing cyber resilience in developing countries: Case studies from Bhutan and Bangladesh. Retrieved April 1, 2025, from https://www.worldbank.org/en/results/2025/01/29/-enhancing-cyber-resilience-in-developing-countries
Yoro, R. E., Aghware, F. O., Akazue, M. I., Ibor, A. E., & Ojugo, A. A. (2023). Evidence of personality traits on phishing attack menace among selected university undergraduates in Nigerian. International Journal of Electrical and Computer Engineering, 13(2), 1943. http://doi.org/10.11591/ijece.v13i2.pp1943-1953
Downloads
Published
How to Cite
Issue
Section
License
Copyright (c) 2025 Joshua Abah Abah, Peter Inalegwu Agada

This work is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License.









